DDOS attacks, ransomware assaults, cyber espionage and data theft – cybercrime in Germany is growing every day and causes damage in the three-digit billion range. Nevertheless, many companies and institutions, especially SMEs, fall short of cyber security requirements.
In order to hold companies, especially those in the critical infrastructure, accountable, the EU Commission has decided to revise and further develop its "Directive on the security of network and information systems". The result is the NIS2 Directive, which will also become mandatory in Germany in the future.
For affected companies, this means preparing for this change in the law and keeping up to date with cyber security. This is because non-compliance could result in high fines and even liability for the managing director or board.
What is the NIS 2 Directive?
The NIS2 Directive is a revised version of the "Directive on the security of network and information systems" (NIS) introduced in 2016. Its aim is to improve cybersecurity standards in the EU so that companies and organizations are better protected against attacks and outages. The original NIS Directive was the first Europe-wide push to ensure a high level of security in essential sectors. NIS2 expands and strengthens this approach to better respond to increasingly complex cyber threats.
In terms of content, the new edition focuses on strengthening the existing national cyber security strategy. The focus here is particularly on companies and organizations that are responsible for critical infrastructures, as their failure or impairment could have significant consequences for society.
The stricter requirements mean that around 30.000 companies in Germany are covered by the NIS2 Directive – significantly more than before. Especially those companies that have not yet been affected by the mandatory implementation of IT security measures must now take action and implement the required procedures.
"Cyber security is central to our society and affects each and every one of us."
Nancy Faser, Federal Minister of the Interior (2024)
Who is affected by the NIS 2 Directive?
The new NIS2 Directive affects significantly more companies and organizations than its predecessor. This means that significantly more companies will have to deal with this regulation in the future. The sectors affected are divided into two areas:
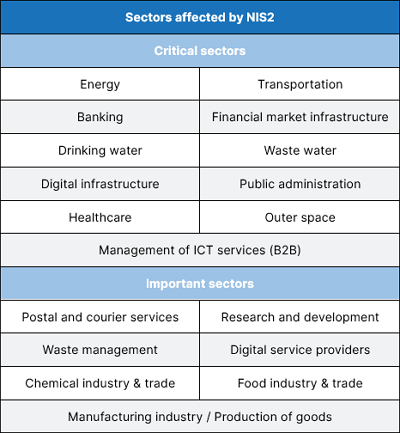
In addition, the size of the company is defined as a criterion for identifying affected facilities. There are two categorie
- Medium-sized companies with at least 50 to a maximum of 250 employees and a turnover of between ten and 50 million euros or with an annual balance sheet total of a maximum of 43 million euros.
- Large companies with more than 250 employees and a turnover of more than 50 million euros or an annual balance sheet total of more than 43 million euros.
Regardless of this, companies can still be affected by the NIS2 Directive. These include – regardless of their size – trust service providers (providers that offers electronic services such as digital signatures to enable secure and legally binding electronic transactions), certain providers of public electronic communication networks, critical infrastructure (KRITIS) and public administration.
It should be noted that the NIS2 Directive now also places greater obligations on suppliers. The reason for this is that the new directive requires the entire supply chain to be secured – both in terms of digital systems and the physical environment of these systems. This means that suppliers may have to set up their IT security to a similar extent as the affected organizations themselves.
How are the new requirements to be implemented?
There are various measures through which the NIS2 Directive can be implemented. These include:
Putting together a project team:
Due to the high requirements, it is advisable to put together a project team to implement the NIS2 Directive and appoint the responsible parties. The information security measures can be coordinated via this team. In addition to IT and security experts, the management should also be involved as well as the data protection officer or a legal advisor.
If there has been little understanding of IT security to date, a joint cyber security training is also recommended.
Introduce an information security management system:
If not already in place, an information security management system (ISMS) should be introduced as soon as possible. An ISMS consists of various policies, procedures and measures that ensure that sensitive information is protected and security risks are controlled and minimized. It can help to identify potential cyber threats at an early stage
The topics that should be considered include:
Define reporting processes and comply with reporting obligations:
The obligation to report a cyber security incident will be tightened once again in the NIS2 Directive. In future, serious security incidents must be reported within 24 hours and a detailed analysis must follow within a further 72 hours of the initial report. Finally, a comprehensive report is due after one month.
In view of these tight timeframes, it can be helpful for companies to establish a reporting process or readjust the existing one. After all, it must be ensured that the relevant information is also available within the defined time frame.
Preparation for stricter controls:
Stricter enforcement mechanisms should ensure that the NIS2 Directive are also implemented to the required extent. Once the NIS2 Directive becomes legal, the supervisory authorities will have more power to monitor companies and impose sanctions in the event of non-compliance. The threat of fines is significantly higher than before.
Note: Regardless of whether your company has to comply with the NIS2 Directive or not, it makes sense to address the issue of data protection. Even if your company is not part of the critical infrastructure, it can still be an attractive target for cyber criminals.
By when must the requirements be implemented?
Across the EU, the new directive has been in effect since early 2023 and was originally supposed to be transposed into national law by the member states by October 2024. In Germany, however, the process was initially delayed. Although the NIS 2 Implementation Act was approved by the federal cabinet in July 2024, the early federal election in February 2025 and the resulting change in government meant that the draft law had to go through the relevant bodies once again.
In May 2025, the European Commission reiterated its demand for the directive to be implemented by the summer of this year. The German government complied with this request and adopted the draft of the "NIS 2 Implementation and Cybersecurity Strengthening Act (NIS2UmsuCG)" on July 30, 2025. At the end of November, the Bundesrat approved the draft accordingly. This officially transposed the NIS 2 Directive into German law, and the provisions are expected to enter into force before the end of 2025.
What are the consequences of non-compliance?
The consequences of non-compliance with the NIS2 Directive should not be underestimated. As a first step, the supervisory authority can initiate supervisory and enforcement measures against the facilities concerned, for example in the form of orders and inspections. The possibility of severe fines cannot be ruled out. Depending on the individual case, the fine can amount to up to ten million euros or two percent of the previous year's global turnover according to the current framework.
It can also be painful for the management, which is explicitly held liable according to the directive. If they do not explicitly take care of the implementation of the necessary legal measures, it is planned to hold them personally accountable. This not only has legal consequences, as company management will also be liable with their private assets in the event of misconduct.
It should be noted that the companies themselves are obliged to find out whether or not they fall under the NIS2 Directive. According to the current status, there will be no authority responsible for the administration and implementation of the directive.
Data protection-ready collaboration software: a building block for NIS2-compliant cybersecurity
The introduction of the NIS2 Directive sets new standards for cyber security and requires companies, particularly in critical sectors, to comprehensively review their security measures. The focus here is also on selecting the right software solutions. If the chosen tool and service providers have taken suitable technical and organizational measures with regard to information security and can prove this accordingly – e.g. with an ISO 27001 certificate – a lot has already been achieved.
Particular attention should be paid to the collaboration software used. A lot of sensitive data is processed in project work in particular, so secure protection of this information is essential. However, NIS2 compliance does not mean that every type of project management software has to be banned from the company. On the contrary, software solutions such as Stackfield not only offer the necessary security, but also actively support companies in complying with the directive.
Data security and encryption:
Stackfield offers true end-to-end encryption for both communication and file exchange. This helps companies to ensure the confidentiality and integrity of their data – a key requirement of the NIS2 directive. It explicitly requires that data is protected against unauthorized access, especially during transmission and storage.
Access control and rights management:
The NIS 2 directive requires strict controls on access to networks and systems. Stackfield enables detailed access rights and role assignments, which means that only authorized users can access certain information and functions. This minimizes the risk of data leaks or unauthorized access.
Data protection in accordance with GDPR requirements:
A clear commitment to data protection guidelines is also part of the NIS2 guidelines, especially when handling personal data. The Germany-based company Stackfield stores all data in certified data centers within the EU, which makes it easier for companies to meet legal requirements in terms of data security and protection. Even Stackfield employees do not have access to company data. In addition, the company has multiple ISO certifications and has received the BSI C5 certificate.
Collaboration and communication security:
The protection of internal communication channels is another focus of the NIS2 directive. All information from the communication channels should be protected from unauthorized access. In Stackfield, the communication options are not only already integrated so that no additional tools are required, but are also certified multiple times for their security.
Conclusion: The NIS2 Directive will change IT security in many companies
With the upcoming NIS2 Directive, the previous cybersecurity requirements will be significantly tightened once again and extended to more areas at the same time. This will be particularly noticeable for those companies and institutions that were not affected by the previous legislation. Suppliers and SMEs in particular are now called upon to make adjustments in terms of IT security.
For them in particular – but not exclusively – it is crucial that they get to grips with the NIS2 Directive and quickly introduce appropriate measures. With sensible investments such as employee training, secure software or a more efficient security culture through an ISMS, a lot can already be done to comply with future legal regulations.